Regulation on identity cards and electronic identity documents (Personnel ID Ordinance-PEV)
Unofficial table of contents
PEV
Date of completion: 01.11.2010
Full quote:
" Staff expulsion order of 1 November 2010 (BGBl. 1460), as last amended by Article 1 of the Regulation of 1 July 2015 (BGBl I). I p. 1101).
| Status: |
Last amended by Art. 1 V v. 1.7.2015 I 1101 |
For more details, please refer to the menu under
Notes
Footnote
(+ + + Text evidence from: 1.11.2010 + + +)
Unofficial table of contents
Input formula
On the basis of § 34 of the Personnel expulsion law of 18 June 2009 (BGBl. 1346) in conjunction with the second section of the Administrative Cost Act of 23 June 1970 (BGBl. 821), the Federal Ministry of the Interior, in consultation with the Federal Foreign Office, orders:
Unofficial table of contents
Content Summary
| Chapter 1 |
General provisions |
| Chapter 2 |
Transmission of the ID application data |
| Chapter 3 |
Production |
| Chapter 4 |
Hand-out |
| Chapter 5 |
Change of data |
| Chapter 6 |
Use of electronic identity verification |
| Chapter 7 |
Blocking and unlocking the electronic identity card |
| Chapter 8 |
Request for permissions |
| Chapter 9 |
Output of authorization certificates |
| Chapter 10 |
Final provisions |
| Annex 1 |
Identity card pattern |
| Annex 2 |
Sample of the provisional identity card |
| Annex 2a |
Replacement Pattern-ID |
| Annex 3 |
Formal requirements for entries in the identity card |
| Annex 4 |
Overview of the Technical Guidelines of the Federal Office for Information Security |
| Annex 5 |
Overview of system components to be certified |
Chapter 1
General provisions
Unofficial table of contents
§ 1 Definitions
(1) A blocking sum is a unique feature which is calculated from the blocking password in accordance with § 2 (6) of the German Personnel ID Act, the surname, the first name and the day of the birth of an identity holder. It is used for the transmission of a blocking from the lock notruf or a personnel identification authority to the lock list operator. With the aid of the blocking sum, the lock list operator determines the lock key of an electronic identity document to be blocked on the basis of the reference list. (2) A lock key is a unique card-specific characteristic that is the result of the calculation of the lock code. a general blocking feature of an electronic identity document to be blocked. It is generated by the identity card manufacturer, transmitted to the lock list operator and permanently stored in the reference list. (3) Authorization certificate provider within the meaning of this Regulation is a natural or legal person who (4) A general blocking feature is a unique card-specific feature, which is a blocked electronic proof of identity in the general Lock list represents. Authorization certificate providers will be sent to convert it to blocking characteristics in accordance with § 2 (7) of the German Personnel Reference Act. (5) The blocking notruf is a facility through which the identity holder can verify his electronic identity document at Allow to include a lock password, family name, first name, and day of birth in the general list of locks. (6) Extensible Markup Language for host documents (XhD) is an extensible page description language (XML) Data exchange format for public documents. (7) OSCI-Transport is the standard for a data transmission protocol defined by the Automated Data Processing Federation/Länder/Municipal area. The standard OSCI transport is to be used in the version set by the Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik), which is made known in the Federal Gazette.
Unofficial table of contents
§ 2 Technical Guidelines of the Federal Office for Information Security
According to the state of the art are to be fulfilled
-
1.
-
the technical requirements
-
a)
-
the storage of the photograph and the fingerprints; and
-
b)
-
access protection to the data stored in the electronic storage and processing media, and
-
2.
-
the technical and organisational requirements
-
a)
-
the collection and quality assurance of the light image and fingerprints,
-
b)
-
the transmission of all identification data from the identity card authorities to the identity card producer,
-
c)
-
the electronic proof of identity and
-
d)
-
the secret number, the blocking and unlocking of the electronic identity card by the identity holder and the storage and erasure of the blocking characteristics and the blocking password, in particular the technical systems to be used in the process, and Communication paths.
The state of the art is to be presumed to be laid down in the Technical Guidelines of the Federal Office for Information Security. These are listed in Annex 4 and are valid in the version published in the Federal Gazette.
Unofficial table of contents
§ 3 Certification
(1) The system components of the personnel identification authorities, the identity card manufacturer, the service provider and their contractor according to § 11 of the Federal Data Protection Act, the certification of which is mandatory or optional, shall be obtained from the Annex 5. The type and details of the certification can be found in the Technical Guidelines of the Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik). (2) For the certification, § 9 of the BSI Act of 14 August 2009 (BGBl. 2821) as well as the BSI Certification Ordinance of 7 July 1992 (BGBl. 1230), as amended. (3) The costs of the certification are borne by the applicant. The BSI Cost Ordinance of 3 March 2005 (BGBl. 519), as amended, shall apply.
Unofficial table of contents
§ 4 Documentation requirements
(1) The personnel identification authority documents for the purposes of the electronic identity document:
-
1.
-
statements by the identity holder to be made in the context of the application and the management of the identity of the identity card;
-
2.
-
the date and time of issue of the identity card;
-
3.
-
the date and time of the handover of the letter with the secret number, the unlock number and the lock password, if the identity card is handed over the letter;
-
4.
-
the elimination of the electronic identity card with the date and time of the elimination, and the identity card authority, which has turned off the electronic identity card;
-
5.
-
the inclusion of the electronic identity card with the date and time of the intervention and the identity card authority, which has switched on the electronic proof of identity;
-
6.
-
the application by the identity holder, the transfer of the blocking sum to the lock list operator and the date and time of the application and transmission;
-
7.
-
the removal request of the identity holder, the transfer of the blocking sum to the lock list operator, and the date and time of the application and transmission.
(2) The blocking notruf documents the application by the identity holder for the purposes of electronic identity verification, the transfer of the blocking sum to the lock list operator and the date and time of the application and transmission. (3) The lock list operator is documented
-
1.
-
in connection with the blocking of the electronic identity card
-
a)
-
the entry of the sperm order with the blocking sum as well as the date and time of receipt,
-
b)
-
the inclusion of the general locking feature in the lock list, as well as the date and time of the blocking,
-
c)
-
the request for the production of the lock list and the date and time of production and
-
d)
-
the actual call as well as the date and time of the actual call, and
-
2.
-
in connection with the unblocking of the electronic identity card
-
a)
-
the entry of the unblocking order with the blocking sum as well as the date and time of the receipt,
-
b)
-
the removal of the general lock feature from the lock list, as well as the date and time of the removal,
-
c)
-
the provision of the list of locks for retrieval, as well as the date and time of the provision, and
-
d)
-
the actual call and the date and time of the actual call.
Unofficial table of contents
§ 5 Storage and deletion
(1) For the storage of personal data pursuant to this Regulation in the case of the staff expulsion authorities, § 23 (4) of the Staff Regulations Act shall apply accordingly. (2) Personal data relating to the lock notruf shall be one year after the date of their collection. (3) The following deadlines shall apply to the storage of the lock list operator:
-
1.
-
The lock key and the block sum are to be deleted from the reference list ten years after they have been entered.
-
2.
-
Updates to the lock list are saved in order to detect the blocking or unlocking of electronic identity documents. They will be deleted ten years after they have been saved.
-
3.
-
A general locking feature will be removed from the lock list ten years after the lock key has been saved to the lock list operator, or if the personnel identification authority has made a lockout.
(4) The identity manufacturer stores the data which has been obtained or generated in the course of the production process and which can be assigned to the requesting person, at most until the lock list operator receives the sum of the blocking sum. and the lock key and the personnel identification authority have confirmed the entry of the lock password. In addition, the data are to be deleted safely. In order to avoid duplication, the identity manufacturer has a list of blocking sums of manufactured personnel cards. The blocking sums in this list shall be deleted ten years after they have been registered. Section 26 (3), first sentence, of the German Personnel Reference Act remains unaffected.
Chapter 2
Transmission of the ID application data
Unofficial table of contents
§ 6 Collection of address
The place of residence in the address referred to in § 5 (2) (9) Alternative 1 of the Personnel Reference Act shall be recorded with the official name and with the unique municipal key used in the official municipal register. Additions to the name of the place of residence shall be included in a uniform manner if this is necessary for the clarity of the place of residence or of the street name. In addition, the postal code is also collected.
Unofficial table of contents
§ 7 Quality assurance of the light image and the fingerprints
(1) From the person for which an identity card is to be issued within the meaning of Section 2 (1) of the Staff ID Code, the personnel identification authority shall submit a current photograph without an edge, which is 45 millimetres high and 35 millimetres wide. If the personnel identification authority has created the technical requirements, the light image can also be
-
1.
-
shall be electronically encrypted and signed by third parties to the Personnel Reference Authority, insofar as this form of transmission is provided for by a Technical Directive of the Federal Office for Information Security, or
-
2.
-
be made by the personnel identification authority.
(2) The personnel identification authority shall ensure the necessary quality of the detection of the light image and of the fingerprint images by means of appropriate technical and organisational measures. For this purpose, it has to examine the fingerprint images and the light image with a certified quality assurance software and to store it in the format used for the ID card. In addition, it is also possible to record the fingerprint images with certified hardware. (3) The light image must show the person in a frontal image, without a head covering and without covering the eyes. In addition, the photograph must comply with the requirements of Annex 3, Section 2. For medical reasons, which are not only of a temporary nature, the personnel identification authority may allow exceptions. From the ban on headgear, it can also allow exceptions for religious reasons.
Unofficial table of contents
§ 8 Transmission
(1) After the Staff Identification Authority has collected all the application data, it shall bring it together to form a digital data record and shall forward it to the identity card producer. The data transmission also includes:
-
1.
-
the quality values of the fingerprints, to the extent that they have been taken off,
-
2.
-
the quality values of the light images,
-
3.
-
the version numbers of the quality assurance software,
-
4.
-
the target values of the quality assurance software,
-
5.
-
the technical characteristics of the stored biometric data in accordance with ISO standard 19794,
-
6.
-
the number of authorities, and
-
7.
-
the time stamp of the expulsion order.
The data transmission is carried out either by data transmission via the information technology networks of the federal government and countries or by means of generally accessible networks. To the extent that the data transmission between information technology networks of the Federal Government and the Länder takes place, it is not later than 1 January 2015 according to § 3 of the Law on the connection of the information technology networks of the Federal Government and the Länder of the Federal Republic of Germany. 10 August 2009 (BGBl. 2706) to use the connection network. The data to be transmitted shall be electronically signed and encrypted in accordance with the state of the art. (2) Suitable valid certificates from the data to be transmitted and to be encrypted by the data to be transmitted in accordance with paragraph 1 shall be valid. (3) The data format XhD shall be based on the data format XhD shall be used for the transmission of the data to the identity card producer referred to in the third sentence of paragraph 1. Data transfer protocol OSCI transport used. The data transmission can also be carried out via switching centers. The bodies involved shall take appropriate measures to ensure data protection and data security, in particular the confidentiality and integrity of the data and the determination of the data security of the data and the security of data protection. ensure that the relevant state of the art is subject to appropriate encryption procedures, including in the case of the use of publicly accessible networks. The Federal Foreign Office may use a different transmission protocol for the transmission of data to the identity card manufacturer. The data transfer between the Federal Foreign Office and its missions abroad must be in line with the requirements of this Regulation with regard to data security and data protection. (4) Prior to the transmission of the identification data Deposit personnel identification authorities, identity card manufacturers and exchanges all technical connection parameters required for electronic and automated communication in the German administrative service directory (DVDV), in particular the certificates required for this purpose. The identity card manufacturer uses a functionality of the DVDV in order to verify the personnel identification authority as such. The Federal Foreign Office can technically independently solve the required technical connection parameters and the associated necessary certificates from the German administrative service directory (DVDV). In terms of data security and data protection, the solution must have a level equivalent to the requirements of this Regulation.
Unofficial table of contents
§ 9 Quality Statistics
(1) The identity card producer shall produce a quality statistic. It contains anonymized quality values for light images and fingerprints, which are determined both in the personnel identification authority and in the identity card manufacturer and evaluated and summarized by the identity manufacturer in the quality statistics. (2) The identity card manufacturer presents the results of the evaluation and, on request, the anonymized individual data collected in the statistics to the Federal Ministry of the Interior, the Federal Office for Information Security and the Federal Office for Information Security. Federal Criminal Police Office at the disposal.
Chapter 3
Production
Unofficial table of contents
Section 10 receipt of the application data
The identity card manufacturer shall verify that the application data has been received in full and without delay, and shall immediately confirm the receipt in electronic form to the identity card authority. It shall take technical and organisational measures to prevent the processing of invalid or incorrectly signed or otherwise erroneous application data. The identity card shall verify the identity of the investigating personnel identification authority.
Unofficial table of contents
§ 11 Model for identity card
The identity card shall be produced in accordance with the model printed in Annex 1. The formal requirements of Annex 3, Section 1, shall apply to the data to be entered.
Unofficial table of contents
§ 12 Sample for the provisional identity card
The provisional identity card shall be produced in accordance with the specimen printed in Annex 2. The formal requirements of Annex 3, Section 1, shall apply to the data to be entered.
Unofficial table of contents
Section 12a Pattern for replacement ID card
The replacement identity card shall be produced in accordance with the specimen printed in Annex 2a. The formal requirements of Annex 3, Section 1, shall apply to the data to be entered.
Unofficial table of contents
§ 13 Interface of the electronic storage and processing medium
The electronic memory and processing medium of the identity card is equipped with a contactless interface and requires the energy supply to be supplied by reading devices for data transmission.
Unofficial table of contents
§ 14 Storage of personal data; protection of access
(1) All personal data stored in the electronic storage and processing medium of the personal identity card shall be protected against unauthorised access. In particular, it shall be ensured that:
-
1.
-
prior to the transfer of personal data, the secret number, the access number or the data of the machine-readable zone (MRZ) must be entered,
-
2.
-
Access rights must be detected by means of authorization certificates and
-
3.
-
all personal data are transmitted in encrypted form between the electronic storage and processing medium and the holders of authorization certificates.
(2) The identity card shall be established in such a way that personal data can only be read by
-
1.
-
authorities that are entitled to establish identity and use a sovereign authority certificate, or
-
2.
-
authorized service providers who use an authorization certificate, after entering the secret number by the identity holder.
Unofficial table of contents
§ 15 Transmission and sending of the blocking password to the personnel identification authority
(1) The identity card shall be transmitted by the identity card in the data transmission format XhD to secure electronic means and shall sign the blocking password for storage in the identity card register. (2) The personnel identification authority confirms to the identity card manufacturer the entry of the blocking password immediately. If the identity card manufacturer has not received any confirmation three working days after he has transmitted the lock password, he shall ask the identity card authority.
Unofficial table of contents
§ 16 Transmission of the blocking sum and the lock key to the lock list operator
The identity card provider encrypts the lock list operator in a secure electronic way and signs the blocking sum and the lock key of an identity card before sending it to the personnel identification authority. Section 8 (1) sentences 3 to 5 shall apply accordingly. The lock list operator shall immediately confirm the receipt of such data to the identity card manufacturer. If the identity manufacturer has not received any confirmation two working days after it has passed the blocking sum and the lock key, he shall ask the lock list operator.
Unofficial table of contents
§ 17 Send of the secret number, the unblocking number and the lock password
(1) The identity card holder shall send the applicant the secret number, the unlock number and the blocking password of the identity card in a letter. The postal address of the issuing personnel identification authority must be given as the sending address. (2) The identity card and the secret number must not be sent at any time by the same post. (3) In the cases of § 13 sentence 3 of the Personnel expulsion law shall be guaranteed by third parties until they are handed over to the applicant for protection against knowledge of the secret number and the unblocking number. (4) The identity card manufacturer shall send the letter in accordance with paragraph 1. the address given in the identity card. If the applicant does not have any flat in Germany, the letter from the identity producer to the issuing authority or to the applicant shall be sent in person to the address designated by it, if the place of residence is in a The State, which the Federal Foreign Office, in consultation with the Federal Ministry of the Interior, has ascertained that it offers reasonable assurance for a proper postal delivery. In the case of letters sent as undeliverable, the personnel identification authority hands over the letter to the person submitting the request. (5) The identity card producer shall draw up and send a letter only if the applicant is at least 15 years and nine months of age at the time of the application. (6) If the applicant has not received the letter, the applicant shall not you can apply for a new ID card. In this case, the letter belonging to the new identity card shall be sent to the staff issuing authority, which shall pass it to the applicant. Paragraph 3 shall apply accordingly. (7) The applicant must, before being given the identity card, confirm in writing that she has received the letter by post or by handing over. The first sentence shall not apply to applicants who do not have a single home in Germany if the identity card is not handed over to them personally by the personnel identification authority.
Chapter 4
Hand-out
Unofficial table of contents
Section 18 Handout of the identity card
(1) The applicant shall declare the electronic identity card not to use the electronic proof of identity. (2) The applicant shall confirm receipt of the letter in accordance with § 17 (3) The identity card holder may at any time obtain the readable personal data stored on his/her identity card at the time of the of a staff identification authority. (4) To read the Data in accordance with paragraphs 1 and 3 shall be used for certified reading devices with a sovereign authority certificate. (5) The personnel expulsion authority abroad may send personnel cards abroad by post to the applicant, if: the collection of the identity card for the applicant would be possible only under unreasonable conditions.
Chapter 5
Change of data
Unofficial table of contents
Section 19 Change of address
(1) The staff identification authority shall change the address on the identity card by issuing a sticker with the new address and the identity card number in accordance with the model in Annex 1. (2) The Staff identification authority shall amend the information on the identity card. (3) For the purpose of modifying the data referred to in paragraph 2, certified devices with a sovereign authority certificate shall be used. (4) The Staff Identification Authority shall change the address in the Replacement ID card in the data fields provided for this purpose.
Unofficial table of contents
§ 20 Replacement and modification of the secret number
(1) In the event that the identity holder does not know the original secret number, the identity card authority may initiate the re-establishment of the secret number by the identity holder. The identity of the identity card holder must first verify the identity of the identity card holder. By means of technical and organisational measures, the personnel identification authority shall ensure that no-one except the identity holder becomes aware of the secret number. (2) The identity holder may enter the secret number by entering the previous Change the secret number and two-time input of the new secret number. (3) Certified devices with a sovereign authorization certificate are to be used for the change in the data referred to in the first sentence of paragraph 1.
Unofficial table of contents
§ 21 Multiple misentry of the secret number
(1) If the secret number has been entered incorrectly twice, a third input attempt can be released by previous entry of the access number. (2) If the secret number has been entered incorrectly three times, the electronic proof of identity can only be if the unlock number is entered and it has not been used ten times. The use of the unlock number is no longer possible after ten times use. If the secret number has been blocked after three times, the re-establishment of the secret number can only take place in the personnel identification authority.
Chapter 6
Use of electronic identity verification
Unofficial table of contents
§ 22 Adorable Power On and Off
(1) Before the issuing or competent personnel identification authority turns off a switched-on electronic proof of identity in accordance with the second sentence of Article 10 (3) of the German Personnel Reference Act, it shall examine the identity of the identity card holder. The Personnel Identification Authority stores the fact of disconnection in the personnel ID register. If the competent personnel identification authority is acting, it shall inform the issuing staff identification authority of the disconnection. In this case, the issuing personnel identification authority stores the fact of disconnection in the identity card register. (2) Before the issuing or competent personnel identification authority has issued an out-of-date electronic proof of identity in accordance with § 10 The identity of the identity holder shall be checked by the first sentence of the first sentence of paragraph 3 of the Staff ID Code. The Personnel Identification Authority deletes the fact of disconnection in the personnel ID register. Where the competent personnel identification authority is concerned, the provisions of the third sentence of paragraph 1 shall apply. The identity card authority initiates the replacement of the secret number by the identity holder upon each subsequent switching-on, and, if desired, informs the identity card of the blocking password from the ID card. (3) For the subsequent entry and exit. Turning off the electronic identity document referred to in paragraphs 1 and 2 shall be used to use certified devices with a sovereign authorization certificate.
Unofficial table of contents
§ 23 Conditions for the use of the identity card holder
(1) Prior to the first use of the electronic identity card, the identity holder shall re-set the secret number once by entering the original secret number sent in the letter. (2) The identity holder shall ensure that: In particular, the following components are used for the use of electronic identity cards:
-
1.
-
information technology systems with appropriate defensive measures against safety gaps according to the state of the art;
-
2.
-
Readers who have been certified by the Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik);
-
3.
-
Software for the use of the electronic identity document, which has been certified by the Federal Office for Information Security.
Chapter 7
Blocking and unlocking the electronic identity card
Unofficial table of contents
§ 24 Reference list; general list of locksates
(1) The lock list operator shall carry out a reference list of the blocking sums, the lock key and the date of transmission of such data from the identity card manufacturer. The reference list shall contain the data of all the identity statements referred to in the first sentence. It may be used exclusively for the determination of the lock key to a transmitted block sum. (2) The lock list operator leads a general lock list. It contains general locking characteristics of locked electronic identity documents and is provided to authorization certificate providers on request for conversion to service-specific lock lists.
Unofficial table of contents
§ 25 blocking of electronic identity card
(1) If an identity card is lost, the identity card holder shall immediately block the electronic proof of identity via the competent or issuing personnel identification authority or the lock notruf, which can also be reached from abroad. . The body through which the identity holder can block the electronic proof of identity as set out in the first sentence shall identify the identity holder prior to the blocking. The blocking may take place without specification of the blocking password, including the blocking password, the name of the family, the first name and the day of birth with respect to the competent or issuing personnel identification authority. (2) The position on which the Identity holders shall block the electronic proof of identity as referred to in the first sentence of paragraph 1, shall immediately generate the blocking sum and shall immediately forward them to the lock-list operator. If the competent personnel identification authority is acting, it shall inform the issuing personnel identification authority of the lock application. The issuing personnel identification authority documents the fact of the blocking in the personnel ID register. (3) The lock list operator must immediately confirm the entry of the general locking feature in the list of blocking lists and to the identity holder forward. If the identity holder can block the electronic proof of identity via the competent or issuing identity card authority, the confirmation shall be made to the issuing staff identification authority. If the identity holder has the electronic proof of identity blocked by the lock, the confirmation shall be made to the lock notruf.
Unofficial table of contents
Section 26 Unblocking the electronic identity card
(1) The identity holder may request the removal of a blocked electronic identity card from the issuing or responsible personnel identification authority. The unlock is performed after identification of the identity holder. The identity holder must appear in person for this purpose. (2) If the competent personnel identification authority is concerned, it shall inform the issuing staff expulsion authority of the removal request. It sends the blocking sum to the lock list operator and deletes the registration of the identity card in the lock list in the identity card register. (3) The deletion of the general lock feature from the lock list is the issuing Personnel identification authority to be confirmed by the lock list operator. The issuing staff identification authority shall forward the confirmation to the identity card holder.
Unofficial table of contents
Section 27 Information on blocking
The lock list operator shall take the technical and organisational measures to ensure that the identity holder receives information as to whether the electronic identity document is entered in the general list of closures. The same information shall be provided to the identity card authority by means of electronic identity cards issued by the identity cards issued by it.
Chapter 8
Request for permissions
Unofficial table of contents
Section 28 Application
(1) In order to be able to verify the existence of the requirements of § 21 (2) sentence 1 of the Personnel expulsion law, an application in accordance with § 21 (1) sentence 1 of the Personnel expulsion law must contain:
-
1.
-
Information on the determination of the identity of legal and natural persons; in the case of natural persons, this is in particular the surname, the first name, the date and place of birth and the address of the main residence; in the case of legal persons these shall, in particular, be the name, address of the registered office, the legal form and the authorised representative; in addition, a copy of the trade register certificate or the instrument of the instrument of establishment shall be annexed in this case;
-
2.
-
Contact details, in particular the telephone and fax numbers, as well as the e-mail address;
-
3.
-
information on applicants with an apartment or seat outside of Germany, to the extent necessary for the unique country-specific identification, including an address-capable address; to the extent that there is an establishment in Germany, shall also include the information referred to in points 1 and 2;
-
4.
-
a description of the service provider and its fields of activity, as well as the indication of the company's website, where available;
-
5.
-
a description of the service offer for which the authorization certificate is to apply, including an indication of the website on which the authorization certificate is used, or the location in the case of vending machines and a reference to the service provided for the Offer valid data protection declaration;
-
6.
-
a sufficient description of the purpose of the data collection for which the authority is to be issued;
-
7.
-
an indication of the categories of data in accordance with Section 18 (3) of the Staff Reference Act, to which the applicant wishes to access; in this connection, reasons shall be given for each category of data as to why it is necessary for the purposes set out above to provide the data for the purposes of: collect;
-
8.
-
Information on the data protection officer (s) according to § 4f of the German Federal Data Protection Act (name, address, telephone number, e-mail address) and to the competent data protection authority (name, seat, address, telephone number, E-mail-address);
-
9.
-
an indication as to whether the applicant is to be served by a contractor in accordance with Article 11 of the Federal Data Protection Act for the purpose of carrying out the electronic identity document and, where appropriate, the information referred to in point 1 for that contractor; This information is not yet known at the time of the application, and it shall be delivered immediately as soon as it is known.
(2) The application shall be signed by the applicant or shall be accompanied by a qualified electronic signature. The applicant shall be identified by:
-
1.
-
the personal appearance and presentation of an official photograph of the applicant, in the case of legal persons of a person entitled to represent a representative, with the awarding authority for authorization certificates or suitable third parties,
-
2.
-
a qualified electronic signature, or
-
3.
-
the electronic proof of identity.
The authority awarding authority determines which of the types of identity document referred to can be used.
Unofficial table of contents
§ 29 Requirements for data protection and security
(1) Requirements within the meaning of Section 21 (2), first sentence, point 4 of the Staff ID Code shall not, in particular, be met if:
-
1.
-
the purpose of the data collection consists solely in the reading out or provision of personal data from the identity card for third parties,
-
2.
-
the State of residence or the registered office of the applicant does not ensure an adequate level of data protection, in accordance with Directive 95 /46/EC of the European Parliament and of the Council of 24 June 2003 on the protection of the applicant's residence or residence. 1 October 1995 on the protection of individuals with regard to the processing of personal data and on the free movement of such data (OJ C OJ L 281, 23.11.1995, p.31),
-
3.
-
the electronic proof of identity for the service provider is carried out by a contractor in accordance with § 11 of the German Federal Data Protection Act and in doing so does not have an effective contractual relationship according to § 11 of the German Federal Data Protection Act between the service provider and the contractor,
-
4.
-
the service provider has chosen a contractor in accordance with § 11 of the Federal Data Protection Act, which is responsible for the technical and organisational requirements of the Federal Office for Information Security in Information Technology for the secure provision of the Electronic identity card is not fulfilled.
(2) The requirements for data security within the meaning of Section 21 (2), first sentence, point 4 of the Staff ID Code are to be fulfilled by the service providers according to the state of the art. The type and scope of the system components to be used determines the authority awarding authority for authorization certificates. The authority awarding authority determines the additional technical and organisational requirements that a service provider has to comply with in order to be approved for the use of authorization certificates. The guidelines apply in the version published in the Federal Gazette. (3) Prior to granting an entitlement to a non-public service provider, the awarding authority for authorization certificates may issue an opinion from the competent authorities. Data protection supervisory authority shall seek to ascertain whether there are circumstances in which there are indications of misuse of the authorisation.
Unofficial table of contents
§ 30 Public list of allowances
The authorization certificate awarding authority publishes a list of all the granted valid permissions. The information according to § 18 (4), second sentence, number 1 to 4 of the German Personnel Reference Act and the period of validity of the entitlement must be published. The data may only be used for the purpose of electronic identity verification.
Chapter 9
Output of authorization certificates
Unofficial table of contents
§ 31 Display of the issuing of authorization certificates
Authorization certificate providers may provide authorization certificates for the electronic proof of identity if they are required to do so prior to taking up this activity.
-
1.
-
the competent authority, in accordance with Section 3 of the Signature Act, has indicated the inclusion of the operation of a certification service pursuant to § 4 paragraph 3 of the Signature Act or has been accredited according to § 15 of the Signature Act,
-
2.
-
the awarding authority for authorization certificates has submitted the notification referred to in paragraph 1 and has made the information referred to in Article 28 (1) (1) to (3), (8) and (9) and (2).
Unofficial table of contents
§ 32 attention to the requirements of the owner of the root certificates
The Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik) is the owner of the root certificates for authorization certificates for electronic proof of identity. The certificate guidelines issued by the Federal Office for Information Security for the technical and organisational requirements for issuing authorization certificates must be complied with by the authorization certificate provider. The guidelines are valid in the version published in the Federal Gazette.
Unofficial table of contents
§ 33 Consideration of authorization by the authorization certificate provider
Prior to issuing authorization certificates, the authorization certificate provider must verify that the authority of the authority certificate authority is granted. It must comply with requirements, restrictions and secondary provisions of the authorization. In case of doubt about the holder, the validity or the scope of an entitlement, he shall inform the awarding authority for authorization certificates before issuing authority certificates. When an authorization certificate is revoked or revoked, the authorization certificate awarding authority informs the authorization certificate provider that the service provider is responsible for.
Unofficial table of contents
Section 34 Validates of authorship certificates
The authorization certificate awarding authority determines the validity period of the authorization certificates with the granting of the authorization. The Federal Office for Information Security lays down appropriate maximum limits for the validity period of authorization certificates. It has to be based on the risk of the sales environment and the requested data categories.
Unofficial table of contents
§ 35 Storage, retrieval and use of data by authorization certificate providers
(1) Authorization certificate providers are obligated to produce lists containing blocking features within the meaning of Section 2 (7) of the Staff ID Code, the current list of general locking characteristics in accordance with § 1 paragraph 4. operate. To do so, they regularly retrieve the list of general locking characteristics, calculate the general locking characteristics in locking characteristics and provide them for the service providers. (2) Authorization certificate providers may use the general blocking lists, which are have been provided by the lock list operator, save and use only until a newer lock list is retrieved. (3) The data from the general lock list may only be used to provide service-specific lock lists with locking characteristics. create.
Unofficial table of contents
Section 36 Issue of sovereign authorization certificates
(1) Freedom of authorization certificates in accordance with Section 2 (4) sentence 3 of the Staff ID Code may only be issued to the authorities entitled to determine the identity. (2) The Federal Ministry of the Interior shall determine which bodies shall be responsible for the identity of the public authorities. (3) The validity period of public authority certificates shall be issued in accordance with the provisions of § 34 sentence of the German Federal Government. 3 of the Federal Office of Security in Information Technology (4) To issue authorized bodies, document recipients, underlying authorization, and the date and time of the issuing of authorization certificates.
Chapter 10
Final provisions
Unofficial table of contents
Section 37 Transitional arrangements
(1) Preliminary ID forms for the temporary staff of Annex 2 to 31 December 2008. The Regulation on the determination of the patterns of identity of the Federal Republic of Germany in force in October 2010 may be up to 31 December 2010. (2) Signature cards issued by the identity card holder to secure the electronic application process of the expulsion authority before 1 November 2010 shall retain their validity until the expiry of the period of validity.
Unofficial table of contents
Section 38 Entry into force
This Regulation shall enter into force with effect from 1 November 2010.
Unofficial table of contents
Final formula
The Federal Council has agreed.
Unofficial table of contents
Annex 1-Sample of the identity card
(Fundstelle: BGBl. I 2010, 1469;
with regard to of the individual amendments. Footnote)
Front

Rear

Sample of the sticker to change the address of the identity card in the issuing form as of 1 November 2010

Pattern of the sticker to change the address of the identity card in the issuing form up to 31. October 2010
 Unofficial table of contents
Unofficial table of contents
Annex 2 Sample of provisional identity card
(Fundstelle: BGBl. I 2013, 342) Sample provisional ID front

Rear
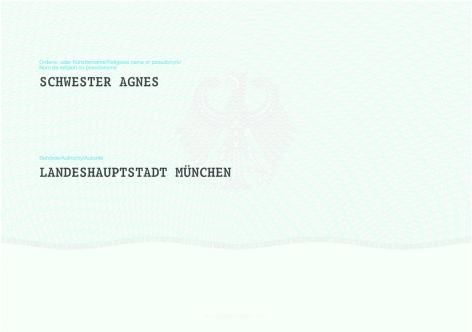 Unofficial table of contents
Unofficial table of contents
Annex 2a-Pattern of replacement-identity card
(Fundstelle: BGBl. I 2015, 1102)
Front

Rear
 Unofficial table of contents
Unofficial table of contents
Annex 3
(Fundstelle: BGBl. I 2010, 1471-1474;
with regard to of the individual amendments. Footnote)
Section 1Formal requirements for entries in the meaning of Section 2 (1) of the Staff Expulsion Law Preliminary notice:
-
1.
-
The requirements for entries described in the table below apply both to the identity card and to the provisional identity card and the replacement identity card.
-
2.
-
Staff identification authorities use to personalize the provisional ID and the stickers to change the address as well as to personalize the replacement staff ID and to change the data of the replacement ID-ID. Font "UnicodeDoc". Ink jet printers can be used for this purpose The ink has to fulfil the properties required by ISO 1831 :1980-10 with respect to machine readability in the B900 band. Only such writing material is to be used, which is in accordance with DIN ISO 12757-1:1999-02 and is authentic and copy-real.
-
3.
-
The character set is the one valid in the respective valid version of the Technical Directive of the Federal Office for Information Security, BSI: Technical Directive TR-03123, XML-Data exchange format for public documents (TR XhD), published The String.Latin character set.
-
4.
-
The machine-readable area in the documents is to be inscribed in the font OCR-B.
-
5.
-
In the data fields "Name" (surname and birth name) as well as "first names" all name components are to be completely represented, as far as this is technically feasible according to the table below.
-
6.
-
In principle, all entries in the documents in the font size 1 are presented in accordance with the following table. If the number of characters available in a data field is exceeded in the font size 1, all the characters of the Should the maximum number of characters available in accordance with the following table not be sufficient, the entries of the data field (for example, the data field) should be used for the data field (for example, the data field). Example first name)-taking advantage of the maximum number of characters available- In the case of the provisional identity card and the replacement ID card, the entry in the data field "Name" of the entry in accordance with the specifications of the following table in font sizes 1 and 2 is allowed in bold. Entries in the other data fields are allowed only in font size 1. If using these font sizes the number of characters available is not sufficient, the entries of the data field (for example, first names) are correspondingly shortened. Different font sizes within a data field are available. In the case of the personalization of the sticker for the change of address on the identity card, the serial number shall be entered in the font size 3. The entries to the postcode, to the place of residence and to the street and house number are to be made in the font size 3 in the fatty set.
-
7.
-
If there is also a birth name in addition to the family name, the birth name must be entered in a separate line. The birth name is the string "GEB." or "geb." with the addition of a blank character.
-
8.
-
To the extent that one or more doctoral degrees are present, this is or are entered in the data field "Name". In accordance with the procedure for the registration of the doctoral degree or The number of remaining characters for the name entry is reduced.
-
9.
-
The alphanumeric serial number of the identity card is formed exclusively from the letters C, F, G, H, J, K, L, M, N, P, R, T, V, W, X, Y, Z, and the digits 0, 1, 2, 3, 4, 5, 6, 7, 8, 9. In the case of the provisional identity card and the replacement identity card, the serial number consists of one letter and seven digits.
-
10.
-
The photograph, which is to be presented by the applicant in the dimensions of 35 x 45 mm, is reduced in the case of personalisation in the provisional identity card with the dimensions 29 x 37 mm.
1
Data field number of characters available
Font Size 1 Badger font font: (2 mm) UnicodeDoc: 2.4 mmFont size 2 Badger font font: (1.3 mm) UnicodeDoc: 2 mm
| Name (surname and birth name) |
26 characters per line;
2 rows (total 52 characters) |
40 characters per line;
3 lines (120 characters in total) |
| First names |
26 characters per line;
1 row (total 26 characters) |
40 characters per line;
2 lines (80 characters in total) |
| Day of Birth |
10 characters per line;
1 row (total 10 characters) |
Entries in font size 2 are not allowed |
| Place of Birth |
26 characters per line;
1 row (total 26 characters) |
40 characters per line;
2 lines (80 characters in total) |
| Nationality |
7 characters per line;
1 row (total 7 characters) |
Entries in font size 2 are not allowed |
| Valid until (last day of validity) |
10 characters per line;
1 row (total 10 characters) |
Entries in font size 2 are not allowed |
| Place of residence |
25 characters per line;
2 lines (total 50 characters) |
Entries in font size 2 are not allowed |
| Street and house number |
25 characters per line;
2 lines (total 50 characters) |
Entries in font size 2 are not allowed |
| Size |
3 characters per line;
1 row (total 3 characters) |
Entries in font size 2 are not allowed |
| Colour of the eyes |
19 characters per line;
1 row (total 19 characters) |
Entries in font size 2 are not allowed |
| Order and Artist Name |
20 characters per line;
1 row (total 20 characters) |
30 characters per line;
2 lines (total 60 characters) |
| Issuing authority |
19 characters per line;
2 lines (total 38 characters) |
28 characters per line;
3 rows (total of 84 characters) |
| Day of the exhibition |
8 characters per line;
1 row (total 8 characters) |
Entries in font size 2 are not allowed |
Data Fields -the sticker for Address change number of characters available
Font size 3 UnicodeDoc: 1,5 mm
| Address |
25 characters per line; 4 lines (100 characters in total) |
| Serial Number |
9 characters per line; 1 line (total 9 characters) |
-
-
The font size is to be aligned with the uppercase letter E.
Section 2
| Pattern photo |
 |
| High-quality photos are the basis for a perfect reproduction of the picture and a prerequisite for the application of facial biometry in personnel statements. This photo-sample is the quality features that ensure the suitability of the photos for the intended use in identity statements. It is urgently necessary to take into account the requirements described here, since otherwise a biometric recognition of the applicant as well as the perfect reproduction of the image in the document are not ensured. The applicant shall, in principle, be represented without a head covering. The expulsion authority may grant exemptions from the requirement of the missing head covering, in particular for religious reasons, from the other requirements for medical reasons, which are not only temporary. No uniformed parts are to be formed on the photos. |
| Format |
 |
| The photo must clearly show the facial features of the person from the chin tip to the upper end of the head as well as the left and right side of the face. The facial height must take 70 to 80 percent of the photo. This corresponds to a height of 32 to 36 millimeters from the chin tip to the top end of the head. In this case, the upper head end is to be assumed with neglect of the hairstyle. Due to the frequently not clearly defined upper head end, however, light images cannot be rejected until the facial height falls below 27 millimetres or exceeds 40 millimeters. In the case of volume-rich hair, care should be taken to ensure that the head (including hairstyle) is imaged as completely as possible, without however reducing the size of the face. The face must be placed centered on the photo. |
| Sharpness and contrast |
 |
| The face must be sharply pictured in all areas, contrasting and clear. |
| Illumination |
 |
| The face must be evenly illuminated. Reflections or shadows in the face as well as red eyes are to be avoided. |
| Background |
 |
| The background must be light-coloured (ideally neutral grey) and have a contrast to the face and the hair. In the case of bright hairs, a medium grey background is suitable, with dark hair a light grey. The background must not have a pattern. The photograph may only show the person to be photographed (no other persons or objects in the picture). No shadows can be created on the background. |
| Photo quality |
 |
| The photo should be available (especially when recording with a digital camera) on high-quality paper with a print resolution of at least 236 points per centimeter (600 dots per inch). The photo must be color-neutral and the skin tones naturally play back. The photo must not have any kinks or impurities. The photo can be in black and white or color. |
| Head position and facial expression |
 |
| A representation of the person with an inclined or turned head (for example, half-profile) is not allowed. The person has to look straight into the camera with a neutral facial expression and a closed mouth. |
| Eyes and eye direction |
 |
| The person has to look directly into the camera in the photo. The eyes must be open and clearly visible and must not be covered by hair or eyeglass frames. |
| Spectacle wearers |
 |
| The eyes must be clear and clearly visible (reflections on the lenses, tinted glasses or sunglasses are not allowed). The edge of the glasses or the frame must not cover the eyes. |
| Head Cover |
 |
| Headgear is basically not allowed. Exceptions are permitted, in particular, for religious reasons. In this case, the face must be visible from the lower chin edge to the forehead. There must be no shadows on the face. |
| Children |
 |
| In the case of children up to the age of 10, the following deviations are permitted at the level of the face and in the eye area: the facial height of children must take 50 to 80 per cent of the photo. This corresponds to a height of 22 to 36 millimeters from the chin tip to the top end of the head. In this case, the upper head end is to be assumed with neglect of the hairstyle. Due to the often not clearly defined upper head end, however, photos are not to be rejected until the facial height drops below 17 millimetres or exceeds 40 millimetres. In the case of infants and young children, the deviations described below also apply. |
| Infants and young children |
 |
| In infants and young children up to the age of 6, in addition to the exceptions presented under the heading "Children", deviations in the head posture (not from the frontal picture!), in the facial expression, with regard to the eyes and viewing direction as well as for centering in the photo. |
Unofficial table of contents
Annex 4 Overview of the technical guidelines of the Federal Office for Information Security
(Fundstelle: BGBl. I 2010, 1475)
-
1.
-
BSI: Technical Directive TR-02102, Cryptographic procedures: Recommendations and key lengths
-
2.
-
BSI: Technical Directive TR-03104, Technical Directive on production data collection, quality testing and transfer of documents for public documents (TR PDÜ hD)
-
3.
-
BSI: Technical Policy TR-03110, Advanced Security Mechanisms for Machine Readable Travel Documents-Extended Access Control (EAC), Password Authenticated Connection Establishment (PACE) and Restricted Identification (RI) [ Advanced Security mechanisms for machine-readable travel documents]
-
4.
-
BSI: Technical Guideline TR-03111, Elliptic Curve Cryptography (ECC) [Elliptic-Curves-Cryptography]
-
5.
-
BSI: Technical Directive TR-03112, eCard-API-Framework
-
6.
-
BSI: Technical Directive TR-03116-2, eCard-Projects of the Federal Government-Hoheitliche AusweisDocuments
-
7.
-
BSI: Technical Directive TR-03117, eCards with contactless interface as a secure signature-creation unit
-
8.
-
BSI: Technical Directive TR-03119, requirements for card readers with the support of the identity card
-
9.
-
BSI: Technical Directive TR-03121, Biometrics for Public Sector Applications [Technical Directive for Biometrics in Sovereign Applications]
-
10.
-
BSI: Technical Directive TR-03123, XML-Data exchange format for public documents (TR XhD)
-
11.
-
BSI: Technical Directive TR-03127, Architecture Electronic identity card
-
12.
-
BSI: Technical Directive TR-03128, Public Key Infrastructures for the electronic ID card
-
13.
-
BSI: Technical Directive TR-03129, Communication Protocols for Extended Access Control [Communication protocols for enhanced access control]
-
14.
-
BSI: Technical Directive TR-03130, eID-Server
-
15.
-
BSI: Technical guideline TR-03131, EAC-Box Architecture and Interfaces [EAC-Box Architecture and Interfaces]
-
16.
-
BSI: Technical guideline TR-03132, Safe scenarios for communication processes in the field of public documents (TR SiSKo hD)
-
17.
-
BSI: Common Criteria Protection Profile Electronic Identity Card, BSI-CC-PP-0061 [Common Criteria-Protection Profile Electronic Identity Card]
-
18.
-
BSI: Common Criteria Protection Profile for Inspection Systems (IS), BSI-CC-PP-0064 [Common Criteria-Protection Profile for Inspection Systems]
Unofficial table of contents
Appendix 5 Overview of system components to be certified
(Fundstelle: BGBl. I 2010, 1476)
System component obligation name nr.Option
| 1 |
Electronic storage and processing medium on the identity card (hard-and software) |
Obligation for the identity card producer |
| 2 |
Fingerprint reader |
Obligation for providers of such equipment
Obligation for the identity card producer
Obligation for staff identification authorities |
| 3 |
Software for recording and quality assurance of the light image and fingerprints |
Obligation for the identity card producer
Obligation for staff identification authorities |
| 4 |
System for the secure transmission of the light image from third parties to the personnel identification authority |
Obligation for the personnel identification authorities, which receive the photograph pursuant to Section 7 (1) sentence 2 number 1 of third parties |
| 5 |
Detection station for the production of the light image |
Obligation for the staff identification authorities to produce the photograph according to § 7 (1) sentence 2, point 2 |
| 6 |
Module for the transmission of data from the personnel identification authorities to the identity card manufacturer |
Obligation for the identity card producer
Obligation for staff identification authorities |
| 7 |
Module to ensure the authenticity and confidentiality of the application data |
Obligation for the identity card producer
Obligation for staff identification authorities |
| 8 |
Change and visualisation module for the change and visualization service in the personnel identification authorities |
Obligation for the identity card producer
Obligation for staff identification authorities |
| 9 |
Card readers for use within the scope of § 18 of the German Personnel Reference Act |
Optional execution by the provider of these devices. Recommendation of the use of certified devices to the identity holder |
| 10 |
Citizen Client |
Optional execution by the provider of this software. Recommendation of the use of certified software to the identity card holder |
| 11 |
Hard-and software for carrying out the electronic identity document with the service providers or their contractors (eID server) |
Obligation for the service provider or its contractor |



 Unofficial table of contents
Unofficial table of contents
 Rear
Rear
 Unofficial table of contents
Unofficial table of contents
 Rear
Rear
 Unofficial table of contents
Unofficial table of contents











